Authentication Providers
Before setting up the authentication providers, make sure you have configured your ADFS/SAML server and downloaded the certificate.
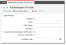
Use the Authentication Providers page to manage multiple authentication providers for user accounts with authentication credentials already established elsewhere.

|
When using authentication providers for users, select the Enable External Auth option in the employee record. |
| 1. | Within the Configuration Console, open the Authentication Providers workspace. The Authentication Provider window appears. |
| 2. | From the New Record Menu drop-down list, choose an authentication provider: |
| Option | Description |
|---|---|
|
New LDAP |
You can employ multiple LDAP providers. See Setting Up Authentication for LDAP. |
| New Open ID |
Open ID providers (Open ID site, Google, Yahoo, etc.) perform the authentication. When logging into HEAT the first time, click the Open ID link. You are redirected to the Open ID site to authenticate. Upon authentication, you are redirected to the HEAT application. See Setting Up Authentication for Open ID. The cookie used for authentication is stored, and subsequent login attempts skip the redirection. |
| New ADFS/SAML |
The customer web portal site acts as the SAML identity provider, and the HEAT Web application server acts as the service provider. See Setting Up Authentication for ADFS/SAML. |
| New Windows Integrated | This option allows you to directly set up AD authentication. See Integrated Windows Authentication. |

|
Ensure that your users are set up to use authentication, as described in Setting Up Users for Authentication. |

|
Use port 389 for LDAP (or port 636 for LDAPS). The protocol for LDAP is TCP. |
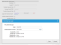
| 1. | On the LDAP Provider page, enter data into the fields. |
| Field | Description |
|---|---|
| Disabled | Saves this configuration without activation. |
|
Name |
Enter the LDAP server name or alias. |
|
LDAP Server |
Name or IP address of the LDAP server used for authentication. If a non-standard LDAP port is used add it to the server name with a colon (serverName:port). |
|
Sort Order |
Specifies the sort order of this provider in relation to other providers assigned to a user. A value of 1 means this provider is used first for authentication when logging in. If a login failure occurs (server failure or incorrect password), the next provider in the sort order is used. The last successfully authenticated login is highlighted in the Enable External Auth area of the Employee record. Use this field only if multiple authentication providers are configured. |
|
Connect to eDirectory Open LDAP Server: |
Select this option to connect to eDirectory and the Open LDAP server. |
|
Use SSL Connection |
Select to allow a connection to a LDAPS server The target LDAP server should also be configured correctly as a trusted certificate authority. If using a LDAPS server which is not a trusted certificate authority, use the Browse button to locate a certificate file, which should contain the fully qualified domain name path of the LDAP profile. |
|
Expiration Date |
Specifies the date that the certificate expires. This field merely stores the date so that you can see when the current one expires and get another certificate before or when it expires. |
| 2. |
Click Save  from the toolbar. from the toolbar.
|
| 3. | From the Employee record, reference the newly created authentication provider. Check the following: |
- The LoginID should be the ID to access LDAP (required).
- Enable external authentication.
- Login for external authentication is populated.
- Reference to newly created authentication provider.
| 1. | Within the OpenID Provider page, enter data into the fields. |

|
Open ID authentication should not be placed first in a sort order for multiple providers because single sign-on logins are not sequenced. Only one is allowed. If the login attempt fails with the Open ID authentication, there is no fallback. |
| 2. | Click Save to save this authentication provider record. |
Before setting up authentication, set up your ADFS/SAML servers.
Make sure you have the ADFS certificate to upload prior to setting up ADFS.
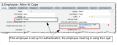
| 1. | Within the SAML Provider page (as described in Authentication Providers), enter data into the fields. |
| Field | Description |
|---|---|
| Disabled | Saves this configuration without activation. |
|
Name |
The tenant ADFS/SAML name. |
|
Identity Server URL |
The URL for the tenant ADFS or SAML. Normally, this is https://<tenant URL>/adfs/ls. |
|
Logout URL |
The URL that users are directed to when logging out of the authentication provider. This is defined on the ADFS computer as the SAML endpoint. Normally, this is https://<tenant URL>/adfs/ls. |
| Don't send parameters, just redirect | |
|
Use SHA-256 Signing Algorithm |
Adds a unique signature using this algorithm only if you did not follow Authentication Configuration of Authentication Configuration. |
|
Force Authentication |
Forces users to re-enter their password when signing in. This option requires users to relogin each time they access the login page, even if they have a valid cookie. |
|
Sort Order |
Specifies the sort order of this provider in relation to other providers assigned to a user. A value of 1 means this provider is used first for authentication when logging in. If a login failure occurs (server failure or incorrect password), the next provider in the sort order is used. The last successfully authenticated login is highlighted in the Enable External Auth area of the Employee record. Use this field only if multiple authentication providers are configured. ADFS/SAML must be the last or only entry in the sort order. After the application redirects to the ADFS site, the application does not have a way of knowing if ADFS failed, so there is no fallback to a different authentication method. |
|
Certificate |
If needed, click Browse to locate a secure signing certificate providing a digital signature for this provider. For ADFS authentication, this is the private key (CER file) installed on the tenant. This is the certificate you obtained in Authentication Configuration. |
|
Expiration Date |
Specifies the date that the certificate expires. This field merely stores the date so that you can see when the current one expires and get another certificate before or when it expires. |
|
Adds new users via authentication. You have the option to auto provision the role, status, and team for the new user. If selected, an Employee record is created if an user logs in using authentication and does not already have an Employee record. The Employee record created will show the Is Auto Provisioned checkbox selected and the Creation Method as Auto Provisioned through SAML by default. |
| 2. | Click Save to save this authentication provider record. |
Upon saving, the authentication record is available for selection when designating external authentication providers in a user record.
Users can click a link on the HEAT login page which directs them to their identity provider website and log in from there to HEAT or users can use authentication to log in from an URL sent via email, as described in Logging In or Accessing Records Using URLs.
| 1. | While logged in as an administrator in the Service Desk Console, open the Employee workspace. A list of employees appears. |
| 2. | Double-click the employee record for which you want to set up authentication. The Employee details page appears. |
| 3. | From the Details tab, select Enable External Auth. |
| 4. | From Login for External Auth, click Add New. The New External Login window appears. |
| 5. | Enter data into the fields. |
| Field | Description |
|---|---|
|
Login |
The login ID for the tenant (UPN) on the domain. |
|
Authentication Provider |
The tenant ADFS that you created. |
| 6. | Click Save. The window closes. |
| 7. |
Click Save  from the toolbar.
Repeat this procedure for each user. from the toolbar.
Repeat this procedure for each user. |

|
When setting up authentication, users must use their external authentication login when logging into HEAT, not their internal login ID. |
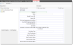
You can temporarily disable authentication providers. When an authentication provider is disabled, it no longer authenticates users and authentication defaults to other configured authentication providers.
The Disabled field is now associated with the FRS_AuthenticationProvider object. Add this field to your form to use this feature:
The Disabled Field in the ADFS/SAML Form