How Discovery and Inventory Auditing Work
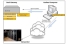
The following diagram illustrates how the different components involved in Inventory Management communicate with each other:
Inventory Management Components
HEAT Discovery is accomplished by:
- An Active DirectoryMicrosoft's Active Directory is a service that stores and manages network-based entities such as applications, files, printers, and people. scan performed from a HEAT gateway.
- Doing a ping discovery on the IP address ranges using a module called Netscan, (included in the data center gateway installation).
- A client agent process called LanProbe, that listens for network traffic and then queries devices on the network using SNMP.
- Gathering data via SCCM and other external sources that communicate directly with the asset processor and other adapters.
- Importing from an external file using the business object uploader.
- Manual data entry.
The following table compares the three HEAT Discovery methods included with HEAT Discovery:
|
Method |
Device Name |
MAC and IP |
OS |
Other |
|
ADScan |
Yes |
Yes |
Yes |
No |
|
Netscan |
Yes |
Yes |
Yes |
Yes |
|
LanProbe |
Yes |
Yes |
Yes |
Yes |
After discovery, assets are audited. Auditing of the discovered assets is accomplished by:
- Installing the HEAT agent on the computer to be audited.
- Remotely auditing via a WMIWindows Management Instrumentation (WMI) is a programming interface (API) that allows devices and systems on the network to be configured, managed, and controlled. Utilizing Common Information Model (CIM), data is collected about system schemas, networks, applications, and devices. scanner that runs on the HEAT gateway.
- SCCMSystem Center Configuration Manager, formerly Systems Management Server, is a systems management software product by Microsoft for managing large groups of computers running Windows, Windows Embedded, Mac OS X, Linux or UNIX, as well as various mobile operating systems such as Windows Phone, Symbian, iOS and Android. import.
- File upload.
The following table compares auditing using the HEAT Discovery agent versus remote scan:
|
Method |
OS Support |
Hardware Information |
Software Information |
Software Usage |
File Information |
Deltas |
|
HEAT Discovery Agent |
Windows and Mac |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Remote Scan (WMI) |
Windows |
Yes |
Yes |
No |
No |
No |
Active discovery involves installing the HEAT gateway on a computer or doing a ping sweep to establish a range of IP addresses which map to live hosts, and then doing an Active DirectoryMicrosoft's Active Directory is a service that stores and manages network-based entities such as applications, files, printers, and people. scan. Passive discovery involves using LanProbe to listen to your network activity and identify new devices when they are added to the network.
The HEAT gateway communicates via HTTPS to the client data web service. The data is in turn processed by the HEAT Discovery processors, which then populate the configuration management database with inventory information. The other way that inventory data populates the configuration management database is from data gathered by SCCM and other external sources, which communicate directly with the HEAT Discovery processors and other adapters.
To run an inventory audit, the HEAT gateway must be installed on one or more computers (or servers) or on a proxy server in your network. To install a gateway, see Installing a Gateway. See Managing Gateway Settings to learn more about your gateway settings.

|
If you are using the HEAT gateway to deploy agents to other client machines, you must have full administrator rights and privileges on those client machines. |
To manage the computers that are currently not audited, you need to deploy a client agent to them, as described in Deploying Agents to Other Computers. This agent allows the subsequent Inventory process to discover all network computers. You can also install agents on remote computers, as described in Installing Agents on Remote Computers.
When the gateway has been installed, it can deploy client agents to other computers. When a client agent has been installed on a computer, it automatically performs an initial full audit (see Running an Active Directory Scan). You can also use the gateway computer to do a remote audit on the client computers without the need to install client agents (see About Running Agentless Audits).
In cases where it is not feasible to install a client agent on a networked computer, you can remotely audit the machine by using Microsoft WMI infrastructure (Windows Management Instrumentation), which allows the gateway to audit computers remotely. Agentless auditing is done by a gateway machine running WMI queries against the target computers. See About Running Agentless Audits.
When data is gathered for inventory either by the agent audit or by remote auditing from the agent or the gateway, the audit data is sent to the HEAT data center web service via a secure HTTPS protocol. The received data is processed in two steps: the raw HEAT Discovery agent data and is processed into a generic format (for example, the names of publishers and hardware are normalized); then the normalized data is populated into the configuration management database.
The HEAT agent and the HEAT gateway also communicate with the task processor to determine if there are tasks to process. The task Processor is a component on the HEAT server, which provides tasks for the gateways and for the clients through a web service. A task for a gateway can be, for example, "install HEAT client on machine X" or "update configuration." A task for a client can be, for example, "update configuration" or "audit computer now."
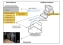
The following diagrams show how data flows from the audited computer to the data center without a proxy and then with a proxy:
LanProbe is part of the inventory agent and monitors your local network activity to collect information from any new IP or MAC devices it discovers. LanProbe detects ip addresses of new ip-enabled devices in a subnet. At minimum, it sends newly discovered devices IP address and MAC address to the HEAT server. If a switch is found on the local subnet, it will be interrogated to find out which devices are connected to each of its ports. The list of discovered devices is returned to the server as part of the audit. When new devices are added to the network, the data is uploaded to the configuration management database and you can decide if you want to deploy agents or audit these devices remotely. See Managing Inventory Settings for more information.