Using Windows Remote Management (WinRM) Setup

|
Before configuring WinRM, be sure that you have a deep understanding of Windows Remote Management. We strongly recommend you review the security implications of each mode. You must have an account with sufficient permissions to use Windows Remote Management before starting configuration. |
| 1. | Check your system requirements. WinRM 2.0 and PowerShell 2.0 are required on the Application Server or on the server where the run program is executed. |
| 2. | Check if PowerShell is installed on the Application Server on which the FrontRange Integration Service is hosted. In Windows, go to Start > All Programs > Accessories and check to see if the Windows PowerShell folder exists. If not, install it per instructions from Microsoft. |
| 3. | Check to see if WinRM is running by doing the following: |
| a. | Run the PowerShell command module as an administrator. |
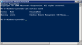
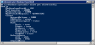
| b. | Enter get-service winrm. |
Windows PowerShell Command Module
| c. | The status should show running. If not, go to Services, change the Startup to automatic, then start the service. |
| 4. | There are two modes: trusted and secure (using an SSL certificate). |
-
Trusted mode: Register the remote server as “Trusted Host” (NOTE: Do not copy and paste. Enter it manually.)
-
Run the PowerShell command module as an administrator.
-
Enter winrm set winrm/config/client ‘@{TrustedHosts=”CA-D02539.NA.FRS”}’.
-
- Secure mode: (using an SSL certificate) Register the remote server certificate using MMC (if necessary).
| 1. | Check your system requirements. WinRM 2.0 and PowerShell 2.0 are required on the Application Server or on the server where the run program is executed. |
| 2. | Check if PowerShell is installed on the Application Server on which the FrontRange Integration Service is hosted. In Windows, go to Start > All Programs > Accessories and check to see if the Windows PowerShell folder exists. If not, install it per instructions from Microsoft. |
| 3. | Check to see if WinRM is running by doing the following: |
| a. | Run the PowerShell command module as an administrator. |
| b. | Enter get-service winrm. |
Windows PowerShell Command Module
| c. | The status should show running. If not, go to Services, change the Startup to automatic, then start the service. |
| 4. | There are two modes: trusted and secure (using an SSL certificate). |
-
Trusted mode: Register the remote server as “Trusted Host” (NOTE: Do not copy and paste. Enter it manually.)
-
Run the PowerShell command module as an administrator.
-
Enter winrm set winrm/config/client ‘@{TrustedHosts=”CA-D02539.NA.FRS”}’.
-
- Secure mode: (using an SSL certificate) Register the remote server certificate using MMC (if necessary).
Use the following steps when using another program to execute Run Program.
| 1. | Check your system requirements. WinRM 2.0 and PowerShell 2.0 are required on the Application Server or on the server where the run program is executed.. |
| 2. | Check if PowerShell is installed on the Application Server on which the FrontRange Integration Service is hosted. In Windows, go to Start > All Programs > Accessories and check to see if the Windows PowerShell folder exists. If not, install it per instructions from Microsoft. |
| 3. | In the PowerShell command module, enable the PowerShell remoting capability by doing the following: |
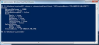
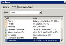
| a. | Enter Enable-PSRemoting -force. This initiates Windows to configure the machine for listener ports and firewall rules. |
Enabling the PowerShell Remoting Capability -- Example 1
Port 5986 is the default HTTPS port used by WinRM to receive the remote commands.
| b. | Enter Winrm get winrm/config to check the configuration. |
| 4. | Create a firewall inbound rule for the port. |
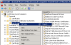
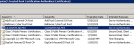
| 5. | Get a server certificate for authentication purposes. |
Trusted Root Server Certificate
| 6. | Get the certificate thumbprint to configure the WinRM listener (in the next step). |
| 7. | Export the public key to register it in the Integration Server. |
| 8. | Configure the WinRM listener. Run the Windows command prompt as an administrator by doing the following: |
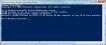
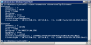
| a. | Enter Winrm create winrm/config/listener?Address=*+Transport=HTTPS @{Hostname=”CA-D02539.NA.FRS”; CertificateThumbprint=”3d448fe37734a891d5876b5c51083c8a79ec0dcb”} |
If successful, the listener shows the port and certificate thumbprint.
| b. | Enter Winrm enumerate winrm/config/listener to check the listener. |
Use the following steps when using another program to execute Run Program.
| 1. | Check your system requirements. WinRM 2.0 and PowerShell 2.0 are required on the Application Server or on the server where the run program is executed.. |
| 2. | Check if PowerShell is installed on the Application Server on which the FrontRange Integration Service is hosted. In Windows, go to Start > All Programs > Accessories and check to see if the Windows PowerShell folder exists. If not, install it per instructions from Microsoft. |
| 3. | In the PowerShell command module, enable the PowerShell remoting capability by doing the following: |
| a. | Enter Enable-PSRemoting -force. This initiates Windows to configure the machine for listener ports and firewall rules. |
Enabling the PowerShell Remoting Capability -- Example 1
Port 5986 is the default HTTPS port used by WinRM to receive the remote commands.
| b. | Enter Winrm get winrm/config to check the configuration. |
| 4. | Create a firewall inbound rule for the port. |
| 5. | Get a server certificate for authentication purposes. |
Trusted Root Server Certificate
| 6. | Get the certificate thumbprint to configure the WinRM listener (in the next step). |
| 7. | Export the public key to register it in the Integration Server. |
| 8. | Configure the WinRM listener. Run the Windows command prompt as an administrator by doing the following: |
| a. | Enter Winrm create winrm/config/listener?Address=*+Transport=HTTPS @{Hostname=”CA-D02539.NA.FRS”; CertificateThumbprint=”3d448fe37734a891d5876b5c51083c8a79ec0dcb”} |
If successful, the listener shows the port and certificate thumbprint.
| b. | Enter Winrm enumerate winrm/config/listener to check the listener. |